Entrust nShield HSM for SSL Decryption for iSSL
The purpose of this feature is to provide the capability for inline-SSL feature to work with HSM hardware. Some enterprises where security is paramount use nCipher HSM to keep the sensitive information such as private keys safe. For the deployments that involves HSM, changes need to be made for how the keys are used during session establishment for inline-ssl feature.
Supported Platforms
| GigaVUE HC1 |
| GigaVUE HC1-Plus |
| GigaVUE HC3 |
PKCS#11 Library
The PKCS#11 (Public Key Cryptography Standards) is a standard programming interface to communicate with HSMs. This standard specifies an application programming interface (API), called “Cryptoki” to devices which hold cryptographic information and perform cryptographic functions.
Proprietary interfaces using Secure Object Library are provided to interact with the HSM for:
| Generating key pair within the HSM. |
| Installing existing key in the HSM. |
| Manufacturing Protection key operations. |
This section provides topics on how to configure and use HSM for SSL decryption for iSSL:
Add at least one HSM appliance by specifying an alias, a static IP address, and port number. Obtain the ESN and KNETI from your HSM administrator.
To add an HSM appliance, do the following:
1. Click Traffic > Inline Flows > Configuration Canvas
2. Click any device.
3. Click HSM.
4. Click Configure Set Key Handler.
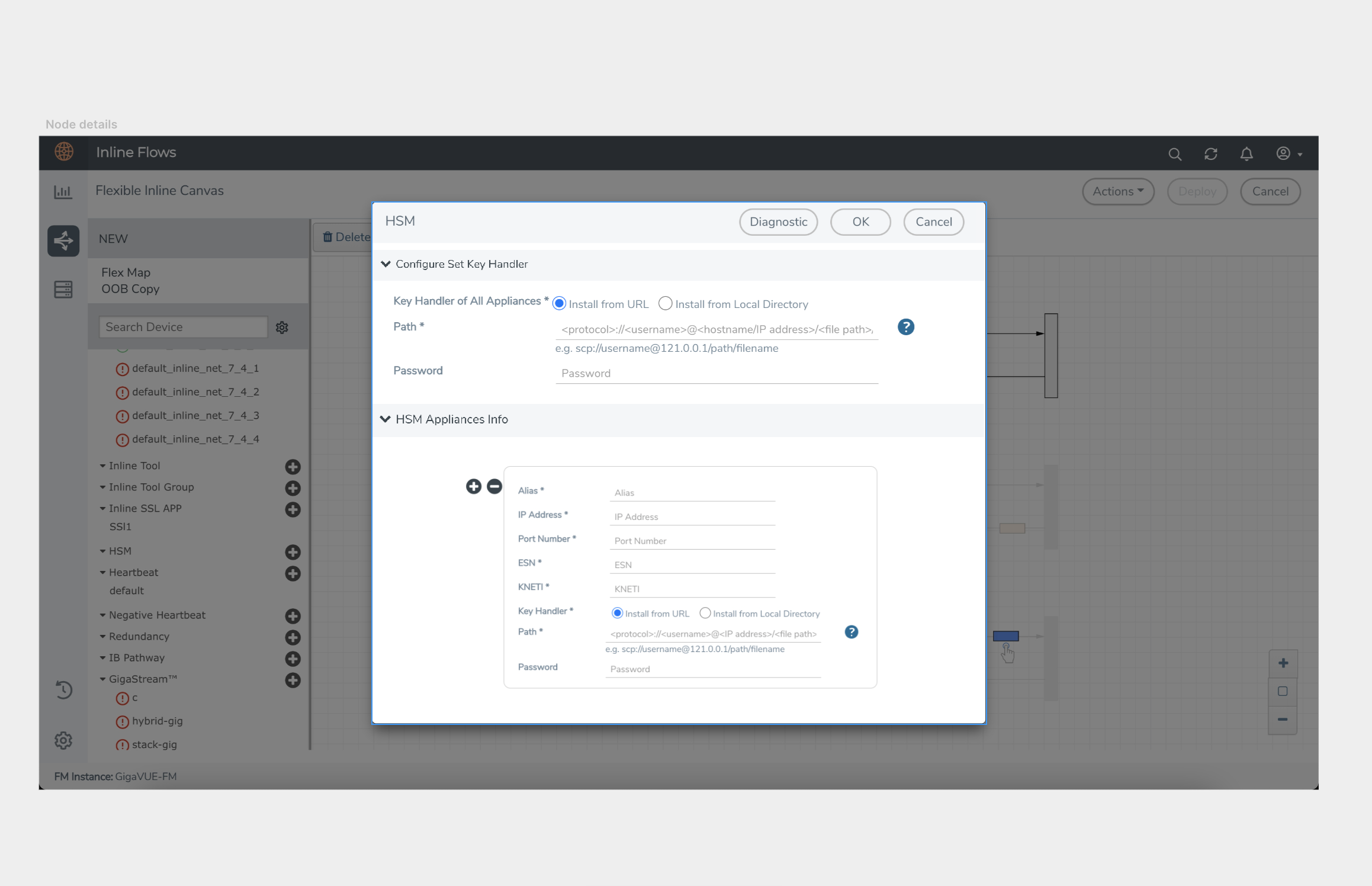
5. Choose one of the following methods to install the key handler file:
| Install from URL—Enter a valid directory path including the file name and enter the password to access the server. |
Note: SCP, SFTP, HTTP, FTP, and TFTP are the supported protocols from where you can select the key handler file.
| Install from Local Directory—Browse and select the key handler file from your local directory. |
Note: Ensure that the file name is "world"
6. In the Alias field, enter a name for the HSM appliance.
7. Enter a valid IP address and Port Number.
8. Enter the ESN and KNETI that you obtained from the HSM administrator.
9. Choose one of the following methods to select the required key handler file:
- Install from URL—Enter a valid directory path including the file name and enter the password to access the server.
- Install from Local Directory—Browse and select the key handler file from your local directory.
Note: SCP, SFTP, HTTP, FTP, and TFTP are the supported protocols from where you can select the key handler file.
10. Click OK.
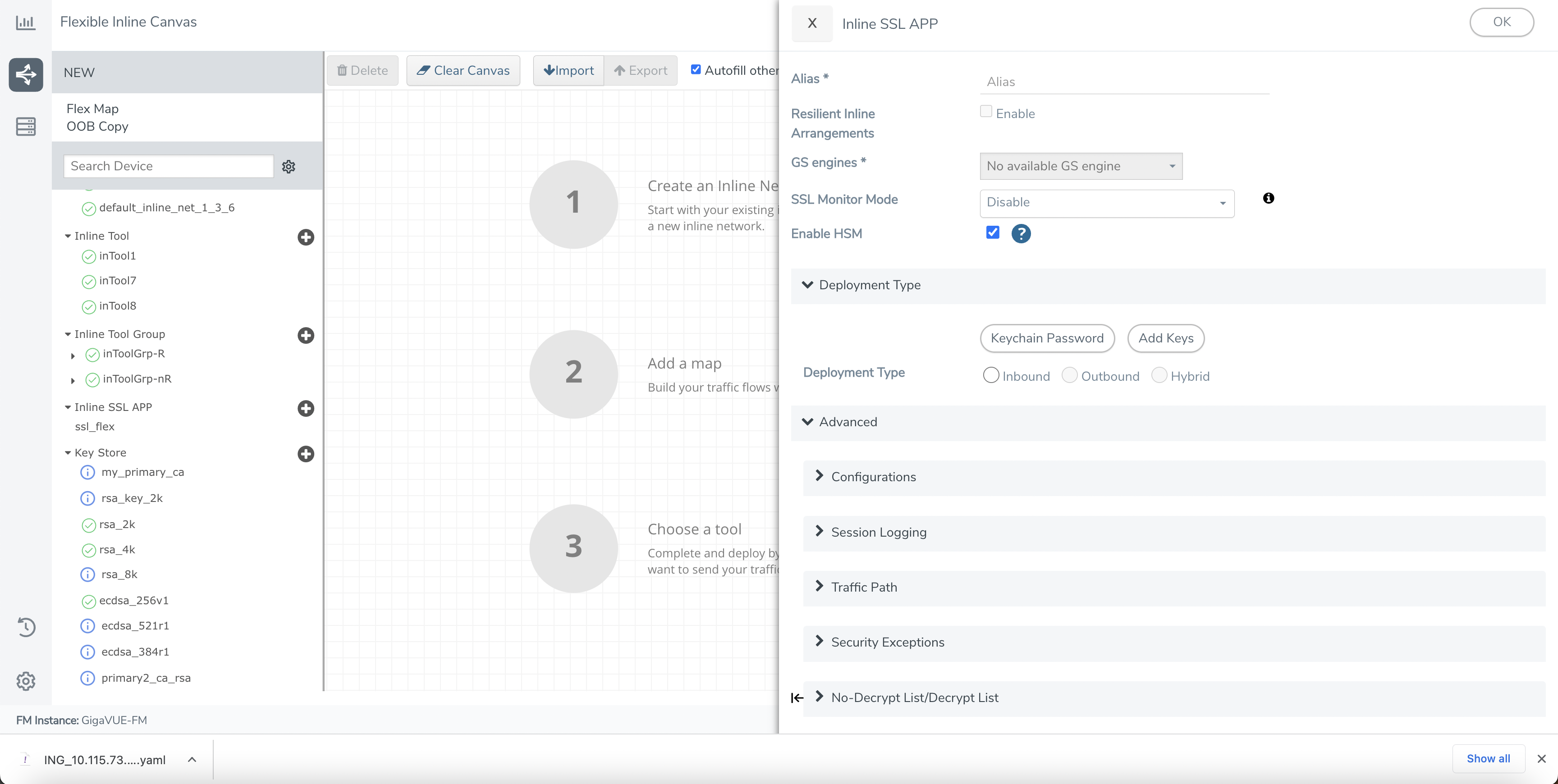
11. You can enable HSM, by checking the Enable HSM check box. The HSM is not supported with Outbound and Hybrid deployment types in software release version 6.2.00
The following image shows the Outbound and Hybrid deployment types disabled for software release version 6.2.00
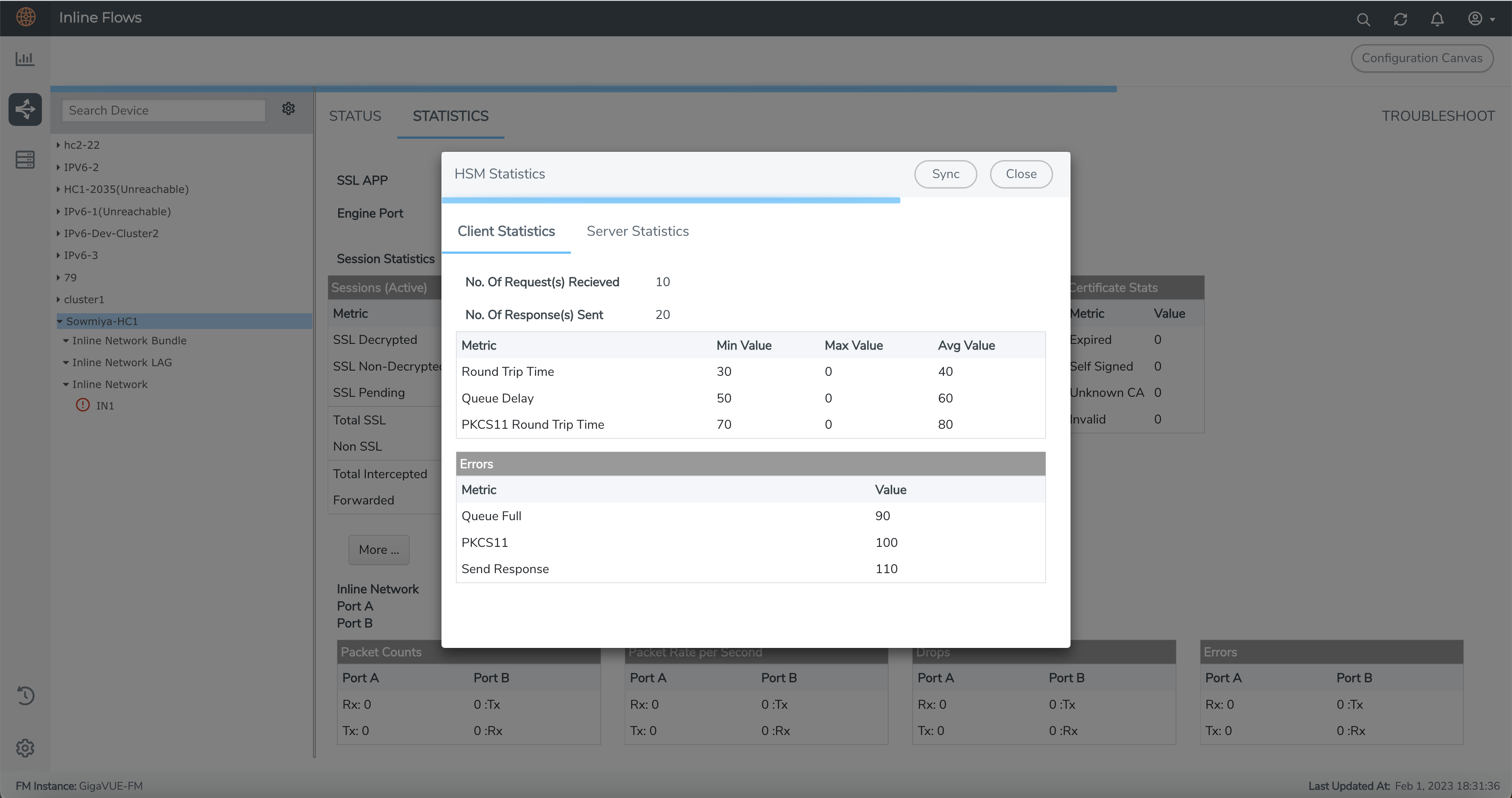
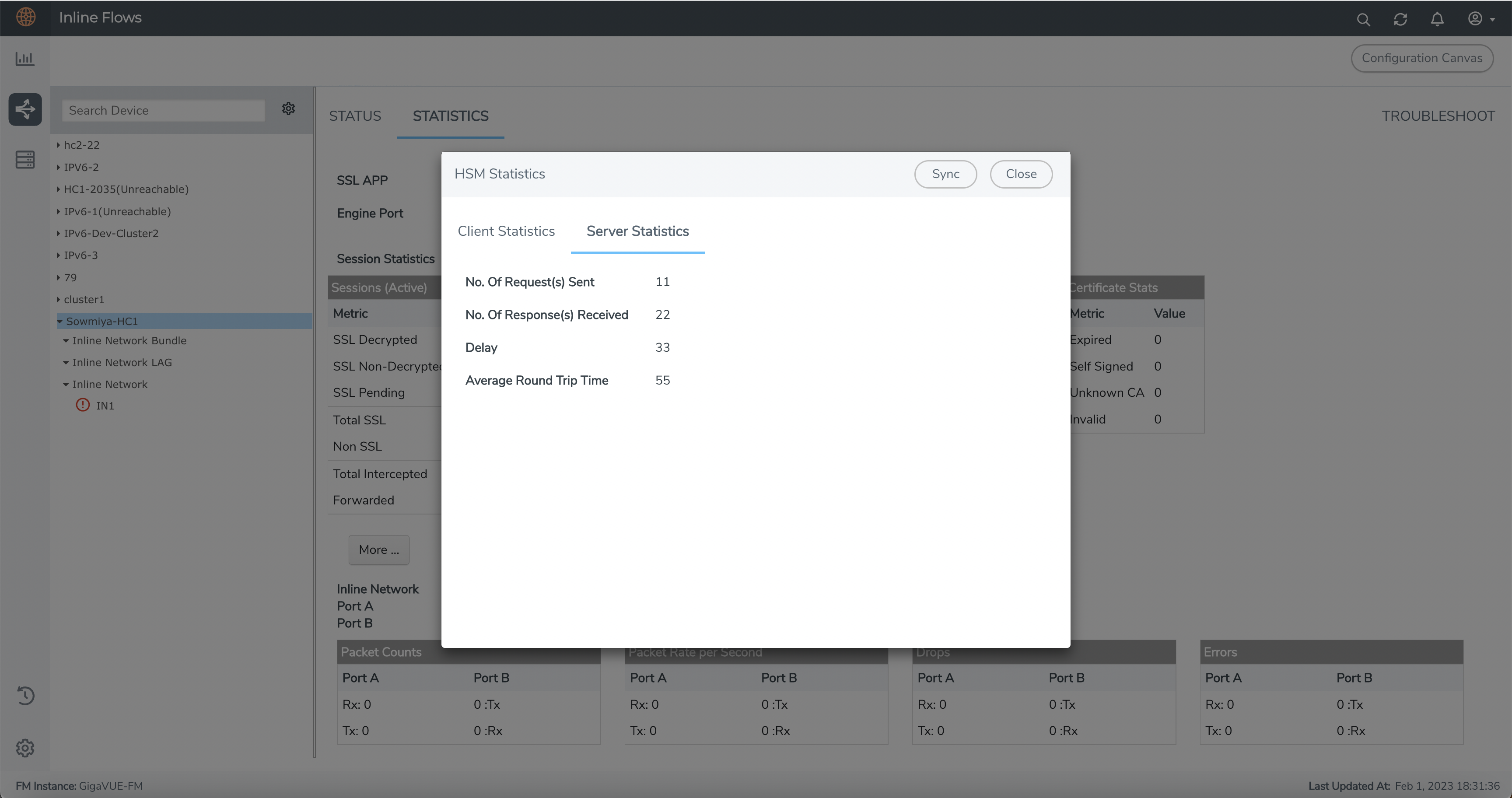
HSM Statistics
You can view the HSM statistics by clicking the STATISTICS tab.
Refer to Configuring Inline SSL with HSM for Key Management for more details.



